Securing your digital communications should be your highest priority when going online. There are just way too many threats to trust any company with your private data. Companies care more about their bottom line than about fixing bugs in their software or poorly under secure data centers. They definitely don’t care if they expose your digital life to harassment, scammers, fraud, and data mining advertisers. Can you actually find a secure messenger app you can trust? And how can you make sure that an app that promises encryption won’t turn evil?
After reading this article, you will know how to choose the most secure messenger app to defeat your conversations against any form of attack you might be likely to encounter.
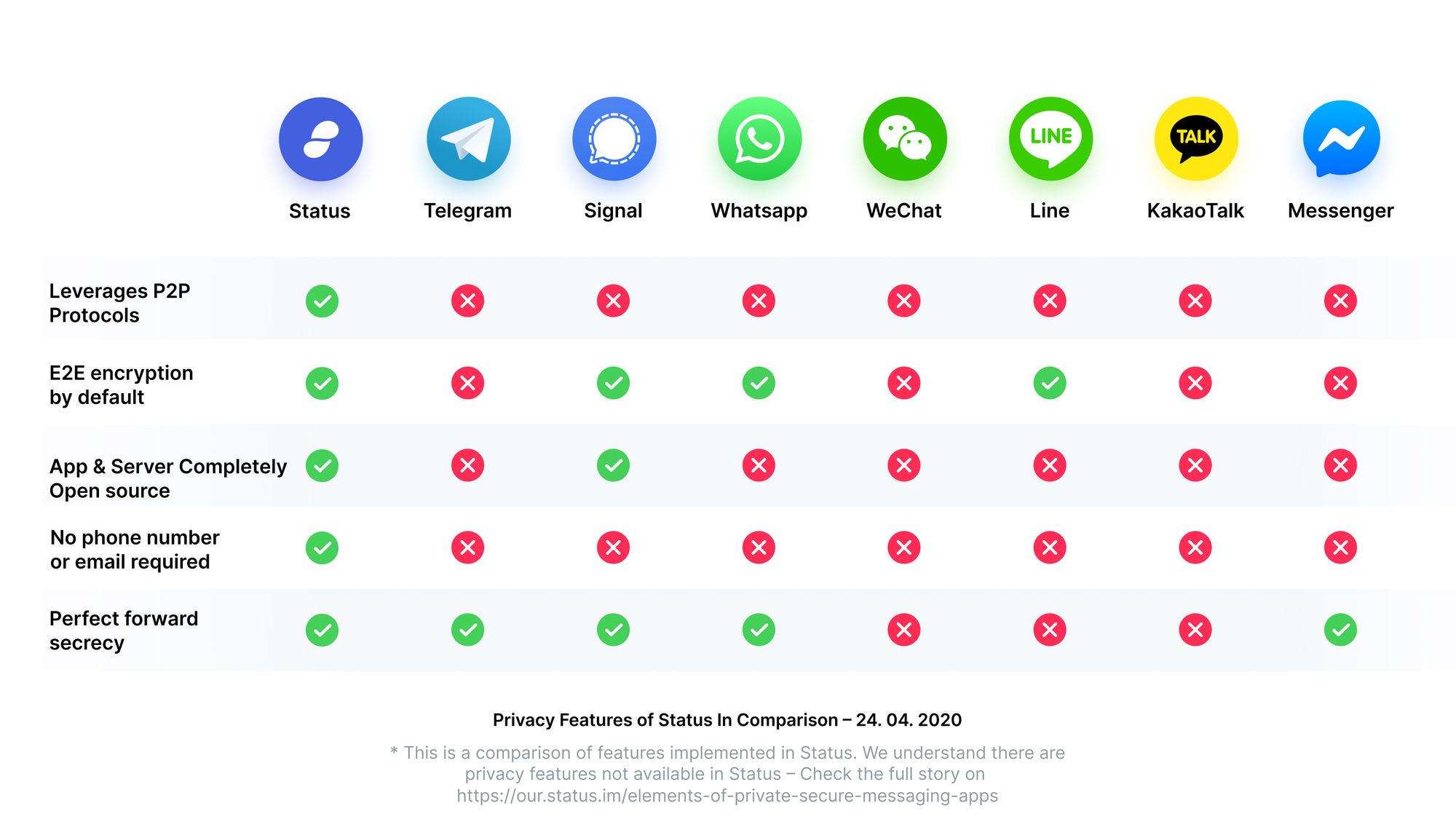
To build our purity test there is a set of questions that can help us filter which apps provide reasonable security and which ones don’t. These questions are listed below:
- Are all messages end-to-end encrypted?
- Is the app fully open source or free software?
- How is the app making money?
- Does it have a good jurisdiction?
- What is the app’s metadata policy?
- Can you create an anonymous account?
- Can you do contact verification?
- Does your app provide disappearing messages?
- Is the encryption strengthened with forward secrecy?
- Is your app in a centralized ecosystem or on a decentralized platform?
Are all messages end-to-end encrypted?
In today’s day and age when data breaches are business as usual, and where Facebook and Google at third parties read your private messages or target their content with ads, it’s absolutely necessary that no one but your recipients can read your conversations. Instant encryption means your message is encrypted before it is sent out from your device and it is decrypted only after it reaches your contact’s device even if it is stored in a database. Only you have access to your decryption keys and there’s no one else who can decrypt your communication.
What we also need to know is whether the app encrypts all conversations by default or whether users have to opt-in by toggling some settings? If the app provides encryption only as a feature that needs to be manually enabled, users will be prone to make mistakes. The best app for security is the one that only sends encrypted messages and doesn’t fall back to plain text mode under any circumstances. However, this is an ideal world. In reality, not all end-to-end encryption has been created equal. Some companies offer snake-hole encryption, where they have access to your encryption keys and thus can intercept your exchange anytime they want. And many others give you promises, but you have to trust their word because they keep the implementation of strong open-source cryptography proprietary that is why intent encryption needs to be immediately accommodated with the next question.
Is the app fully open source or free software?
This isn’t just a question of licensing. The most secure designs are the ones you don’t have to trust. When developers of secure systems hide their source code, we can’t verify whether they didn’t build a backdoor into their implementation. And they cannot prove that their messaging app is truly secure. But don’t be fooled by false advertising. Just because an app uses open-source cryptography doesn’t mean it’s fully open source. Most still keep the rest of the source code including the implementation of open-source encryption hidden, especially commercial apps like iMessage or WhatsApp offer way too many features that make their source codes too complex for a single company to patch all the bugs. The more eyes on the code, the more secure it becomes.
How is the app making money?
Cryptographers and developers are expensive. Maintaining servers that handle a lot of content and bandwidth isn’t cheap either. Who is paying for all that? Usually, the saying goes, if it’s free, you’re the product. But in the world of open-source, that is not necessarily the case. Many open source app developers are part of nonprofit organizations, and they tend to live off a donation in sponsorship. Some do have a business model where they make money somewhere else by offering premium versions or selling hardware. If the team behind an app is publicly facing, and you can verify who they are and how they earn a living, they most likely take security seriously. If they are hiding behind good PR and corporate speech and you can’t find out who is back in them, or their company is in the advertising business, that’s a red flag.
Where is the organization’s jurisdiction?
This applies to where the company is illegally registered? Where they conduct business from and where they host user data? Every internet service is going to handle some user data for some period of time. They could be forced by law enforcement to lock their users or hand over any data to the government. As a general advice, it is recommended to avoid providers from the five eyes surveillance Alliance. But that on its own is in this qualifying if the organization can prove they don’t retain any sensitive or potentially incriminating user data which leads to our fifth question.
What is the app’s metadata policy?
This can be found in privacy policies published directly on their websites. We call it metadata policy because that’s our biggest concern with encrypted apps. You must read what information they collect as well as whom they share your data with. The general rule of thumb is: “the shorter the policy, the better.” If it spans out on several pages explaining how they handle every bit of data they collect, this is a big sign to stay away from it. The best privacy policy states: “we do not collect any user data, and we delete all the data once no longer necessary to deliver the message.”
Can you create an anonymous account?
This is going to be important to some people more than others. If you are targeted by someone who knows your identity, like the government or the Italian mob, then you want full anonymity. If your app requires a phone number or an email, you are not anonymous even if you can get a burner sim, it’s still associated with your general location. Emails can be anonymous if only they were created overt or never exposed to the clear net, which is something that isn’t so easy to achieve. The most anonymous account creation is one where we can download the app over tor connection outside of Google Play Store or Apple App Store, create an anonymous identity straight away, and run the app over toward at all times. Only a handful of apps meet these criteria, but you might not need it unless you expect to be targeted. Your communication can only be as secure as its weakest link. If you can’t verify your contact’s identity, someone can hack into your contact’s account and read your conversations or even pretends to be your contact, which is why you need to ask the next question.
Does my secure messenger offer contact verification?
If you’re a newcomer to privacy, contact verification may be a novel concept for you, but it is a powerful feature that can prevent hackers from taking over your conversations. Contact verification usually takes the form of comparing fingerprint codes over a phone call or scanning each other’s QR codes in real life. And if a hacker logs in with a new device, your app will alert both of you about their new unverified device. If you can’t 100% rely on the physical security of your device, you should ask the next question.
Does your secure messenger provide ephemeral messages?
Self-destruction messages is a neat feature that gives you the peace of mind that even if you lose your phone, your conversations will be automatically deleted after a preset expiration of time. This can be anywhere from weeks down to just a few seconds. But if your adversary obtains your private decryption key from your device and they already capture your encrypted messages, then they could decrypt your conversations. But not if your app generates a new encryption key for every message so that even if the keys from the last message are compromised, they can be used to decrypt past conversations and that’s why the next question of the purity test should be asked.
Does your secure messenger app encryption provide forward secrecy?
In the long run, encryption is nice and all, but without freedom, your security will have a single point of failure. It is important to know: Is your app in a centralized ecosystem or on a decentralized platform? The meaning of decentralization has multiple levels. If all the data flows through the central servers of your app provider, then you have to trust them with their metadata. If you can host your own instance or choose a different server, you have the freedom to delegate trust to someone else in some other jurisdiction. If your app is fully peer-to-peer, then there are no central servers to compromise, and there is no single point of failure. If your app is open-source, is it also federated? Meaning does it allow its spin-offs and other apps to communicate with their users? Or is it locked down like most messaging ecosystems? Federation lets you take the most secure encryption protocol and use it to securely communicate with users of other apps. So that none of you has to rely on any single provider. Federation is the future of the Internet, or at least that future that doesn’t turn into a tech dystopian nightmare.
Conclusion
In a nutshell, most people’s threat models should allow them to choose a messaging app that is open-source but also easy to use. So that it won’t make any security mistakes. If you think you might be targeted by your name you should go for an anonymous peer to peer app that doesn’t have any central weakness.
If you have an app idea for building your customized secure and private messenger, contact AminSoft to take advantage of our free and confidential app consultation. Also, you can trust our experienced developers to develop your own professional and secure messenger which suits your business. Your messenger will be customized to your needs, and it can be extended by any individual features.